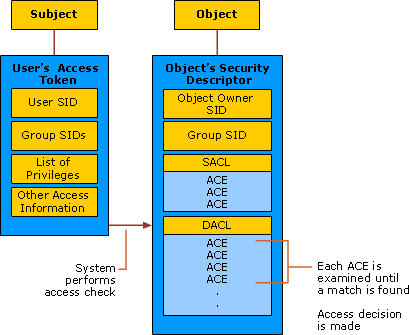
I apologize for my presumption, but thought it was a cool title 😉 Some days ago, I was reflecting on the SeRestorePrivilege and wondering if a user with this privilege could alter a Service Access, for example: grant to everyone the right to stop/start the service, during a "restore" task. (don't expect some cool bypass or exploit…
Demystifying Windows Service “permissions” configuration